While Zero Trust has been around for many years, the move toward digital transformation, ubiquitous connectivity, the move to cloud, remote work and government mandates have significantly elevated its importance. These drivers, as well as new delivery and consumption models, contribute to an evolving perimeter and expanded attack surface, providing more opportunities for threats to arise.
Palo Alto Networks is the global cybersecurity leader. As you can imagine, we see thousands of attempted attacks per day. Like our customers, we are subject to the same business drivers that I mentioned above. The combination of those drivers and an eroded perimeter means that we needed a deliberate, standardized and, most importantly, automated approach to cybersecurity. Zero Trust was our response. Here’s what we learned on our own journey.
Defining Zero Trust
Like many, we had to eliminate the noise around Zero Trust and determine what the term actually meant. We defined Zero Trust as a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction.
How did we end up with that definition? First, many years ago, the majority of people worked in the office and there was the traditional “hard perimeter” network model. It was difficult to get through the “hard shell” or firewall, but once in, users were trusted. With digital transformation, the move to cloud and hybrid work, the hard shell has been significantly eroded.
Today, users need access from anywhere with the same level of security everywhere. Now, rather than security following the perimeter or physical building, it must follow the user and the data, wherever they are.
Next came legacy trust for users. Legacy trust is the model whereby a user is authenticated via their username and credential, and they’re trusted for a long period of time, i.e., hours to months. If a user’s passwords are compromised, then the authenticated attacker may have free reign to move laterally in your internal networks for months.
Zero Trust instead is based on the model that a user is questioned at every access point. At Palo Alto Networks, users are continually validated wherever they go – from networks to email to SaaS applications and cloud environments. These two situations helped us encapsulate our definition of Zero Trust.
Making Zero Trust Actionable — Identifying Key Steps in Our Zero Trust Enterprise Journey
We understand that implementing Zero Trust isn’t easy, but getting started shouldn’t be hard. We take a holistic approach to our Zero Trust strategy – the Zero Trust Enterprise. With a comprehensive set of security capabilities, the Zero Trust Enterprise introduces consistent Zero Trust controls, eliminating implicit trust across the organization.
While on our Zero Trust journey, we identified four important steps that we feel could help any organization with their Zero Trust effort:
- Identify Your Crown Jewels – We began by identifying our “crown jewels,” meaning our most sensitive data. This is the data critical to maintaining operational continuity, availability and quality of service. We determined our crown jewels to be intellectual property, source code and supply chain information. Of course, specific crown jewels will be different for every industry. For example, in public sector, it’s likely to be government intelligence. For the financial industry, it is usually customer data and payments. For pharmaceuticals, it’s likely drug composition and supply chain. For the retail industry, it’s probably consumer packaged goods and inventory management.
- Know Where Your Crown Jewels Are Located… Always – Next, we determined where that highest-priority data resided, because we can’t protect what we don’t know. What applications did it live on? On what infrastructure did those applications reside? Were they in house, SaaS or part of our supply chain? Additionally, how was the data accessed, and by whom? Once all of these questions were answered, we could then map each element to a Zero Trust strategy.
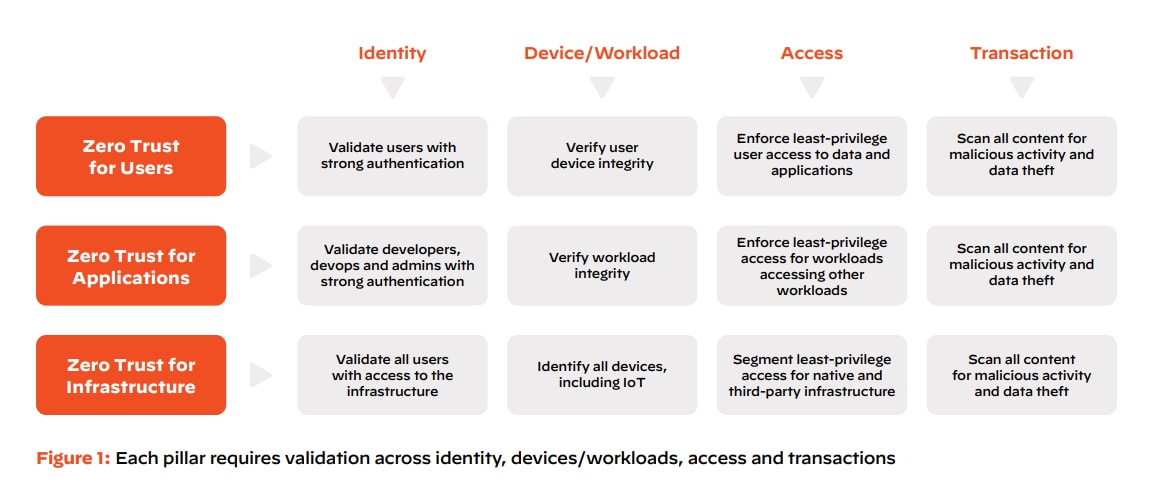
- Apply Zero Trust Where It Matters – As I mentioned earlier, at its core, Zero Trust is about eliminating implicit trust across the organization. Our next step was eliminating implicit trust related to users, applications and infrastructure.
Users: Applying Zero Trust to users starts with strong identity controls that must be continually validated for every user activity, using best practices, such as multi-factor authentication, adaptive authentication and just-in-time access. Without strong identity management, Zero Trust policies and controls are much less effective.
Applications: Applying Zero Trust to applications removes implicit trust with various components of applications when they talk to each other. A fundamental concept of Zero Trust is that applications cannot be trusted and continuous monitoring at runtime is necessary to validate their behavior.
Infrastructure: Organizations have often responded to each emerging threat with a new tool or technology. This heterogeneous environment means that IT teams are often overwhelmed and have poor visibility and control over unmanaged resources, such as IoT devices and supply chain infrastructure. In fact, both of these have been major factors in recent high-severity security breaches. That means for everything infrastructure-related (including routers, switches, cloud and especially IoT and supply chain resources) eliminating implicit trust is even more critical and must be addressed with a Zero Trust approach. An example of this is if an attacker compromises an HVAC system (infrastructure) and is not automatically trusted to move laterally and attack a financial application or end user account.
4. Manage Zero Trust Through Automation – While many organizations are dealing with a chaotic security model that involves dozens of point products generating an enormous volume of alerts connecting into different technology stacks, we used Zero Trust as an opportunity to consolidate tools and automate security. We now put everything through our Zero Trust Model, from authentication to least-privilege access, to device security, to content scanning. This is hugely powerful. Consolidation enables full automation, so everything is analyzed, and only the important items are elevated to our security operations center (SOC) team.
Leveraging Automation as a Zero Trust Accelerator
This platform and automation approach has enabled us to deliver an industry-leading, one-minute response time. The vast majority of companies struggle with days, weeks, months or even years to detect and respond to a critical event.
Each day, our SOC processes nearly 17 billion security events. Our Palo Alto Networks Cortex XDR application reduces these events to an average of 467 alerts. From those 467 alerts, our automated Palo Alto Networks Cortex XSOAR platform reduces them to just 67 incidents needing analysis. Fifty-eight of those are automatically remediated by XSOAR. The remaining nine are enriched with additional data and are then forwarded to a SOC analyst to triage, due to their criticality. From 17 billion to nine, the SOC can now find the needle in the haystack within one minute, and they are free to focus on high-value events, like proactive threat hunting, rather than being overwhelmed by alert noise.
This one-minute-to-respond time enabled Palo Alto Networks to be the first company to detect, prevent and respond to the SolarWinds industry attack in 2020. We were deploying Zero Trust when the attack occurred. Using Cortex XDR, we detected the attack within 10 seconds. Within one minute, XSOAR routed the alert to the SOC and an expert was logging in to validate the issue and take the system offline. Our detection and notification to SolarWinds came two months before any other security provider was able to do so.
Reaping the Benefits of the Zero Trust Enterprise
The Zero Trust Enterprise delivers simplified security because there is only one use case: continuous validation across users, applications and infrastructure. No matter where our users are, what they try to do, where they go, where the application is, etc., the security level is the same. The same thing is true for securing applications. We treat our traditional data center applications, private and public clouds, our SaaS applications and everything infrastructure-related the same way. We gain a far better security outcome with a simplified infrastructure and security architecture, based on Zero Trust
Ultimately, Zero Trust isn’t a flip-the-switch effort to enhance cybersecurity. It takes time, and in truth, it’s a continual journey. In taking such an extensive, methodical approach to Zero Trust, we simplified security operations and significantly reduced risk and complexity while driving greater operational efficiency through lower overhead and automation. We advanced Palo Alto Networks from being cyber secure to being truly cyber resilient – having the ability to help anticipate, withstand, recover from and adapt to cyber-adverse conditions.
Find out how we can help your organization become cyber resilient through Zero Trust.